Topic
Examples of Use
There are many note-taking applications, but this tool is useful when you need to encrypt specific parts of your
text.
For example, it can be used for secure password management.
For an example of password management with Notion, check out the following blog.

Password Management with Notion
How to manage passwords using Notion. Passwords are stored in encrypted form.
View DetailsStructure
Encryption and decryption are performed entirely in the user's browser, ensuring that no data is sent to the
server.
The encrypted data is embedded in the parameters of the decryption URL.
This app uses PBKDF2 to generate an AES key from the passphrase entered by the user.
A random salt is processed through the HMAC/SHA-256 hash function 100,000 times. (The number of iterations can
be adjusted.)
The data is then encrypted using AES with the generated AES key and an initialization vector (IV).
Similarly, this app allows decryption by entering the correct passphrase.
| TXT-Crypter | Evernote | |
|---|---|---|
| Key generation | PBKDF2 | PBKDF2 |
| Number of iterations | 100,000 times or more | 50,000 times |
| Encryption | AES - 256bit | AES - 128bit |
Security
Keep the decryption URL in a location that only you can access.
As long as the URL is not shared with others, unauthorized decryption is impossible.
Even if someone obtains the decryption URL, they cannot decrypt the data without knowing the passphrase.
Attackers may attempt brute force or dictionary attacks.
A weak passphrase increases the risk of unauthorized decryption, so choose a strong one.
This app provides a method for manual decryption. (Of course, a passphrase is required.)
This ensures that you can still decrypt your data even if this app becomes unavailable.
On the other hand, you may be concerned about unauthorized decryption.
Even if your passphrase is not easy to guess, consider whether it could be cracked through brute force attacks.
Take, for example, a 4-digit combination lock.
There are only 10,000 possible combinations from 0000 to 9999.
Even if you forget the code, you could eventually unlock it by trying every number in sequence.
If you enter an 8-character passphrase consisting of uppercase and lowercase letters, numbers, and 32 symbols,
there are 6,095,689,385,410,816 possible combinations (94^8).
On my PC (Core i5 11th generation), with the default iteration count of 100,000, each encryption takes
approximately 800ms.
For simplicity, assuming 2 attempts per second, only 172,800 attempts can be made per day.
At this rate, even with a brute-force attack, it would take about 100 million years to guess the passphrase.
Since even an 8-character passphrase results in such an enormous number of combinations, increasing the length
further will exponentially increase the complexity.
Additionally, increasing the number of iterations will make each decryption attempt slower, significantly
extending the total brute-force time.
An attacker would not only need to brute-force the passphrase but also the number of iterations.
At this point, we can be quite confident in its security.
After reading this far, you may conclude that the possibility of unauthorized decryption is almost zero.
But what if it does get decrypted?
The text you encrypt should never include a combination of a site name, ID, and password.
For example, each encryption should contain only the password.
Even if an attacker manages to decrypt the password, they would still have no information about which site it
belongs to or what the corresponding ID is.
However, as mentioned earlier, Evernote also uses PBKDF2, and when implemented correctly, it does not pose a significant security risk.
That said, I am interested in Argon2, and I may consider adopting it in the future.
Manual decryption
In the unlikely event that this app becomes unavailable, you can still manually decrypt your data using the
decryption URL.
The source code for decryption is available on GitHub.
Download decrypt.html and open it in your browser.
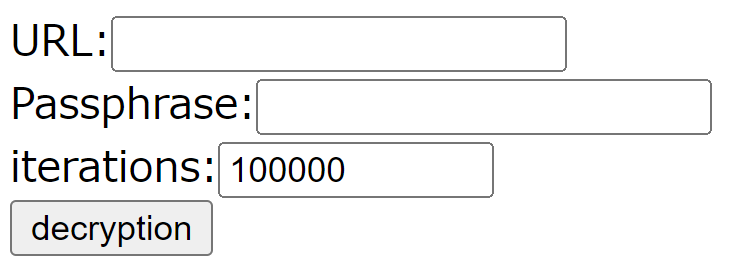
Enter the decryption URL, passphrase, and number of iterations, then click the 'Decryption' button.
If the information is correct, the decrypted text will be displayed.
This ensures that you will always be able to decrypt your data, even if the app is no longer available.